We all remember the Nigerian prince email scams. These were popular years ago, but they’re still around. For those who haven’t had the good luck to receive one…a Nigerian prince has a large sum of money or a fabulous investment opportunity and you are the best person suited to help. You thank your lucky stars that the prince chose you, and immediately forward him your personal info.
I got a good chuckle just thinking about it until I did some research and found that not only is this email still making the rounds, many people are still being defrauded out of large sums of money. Click here.
I shouldn’t laugh. I’ll talk in upcoming posts about a couple of scams of which I was the target and in the heat of the moment, it can be emotional. (I’ve since added that post here). But back to the prince, email scams are everywhere. Why? Because they work.
How and Why Do Email Scams Work?
Reason #1 is volume. It really isn’t a prince in Nigeria who tracked you down and chose you specifically. It is likely a big corporation that exists for the sole purpose of defrauding people like you and I. The technology and data that is available to these folks is astounding.
They have complex computer systems that send millions of emails in a formatted template. And where does an aspiring young criminal get email addresses? The dark web is a great spot. Check this out. You can buy or sell anything. But you don’t need to be this devious. There are legitimate ways that marketing firms buy and sell email address lists.
Millions of emails go out and they only need one or 2 responses to make this worthwhile.
Reason #2 is somewhat age dependent. For many of us, it is our nature to respond to a request. My mom was a favorite target of these folks. I noticed that she and her friends would often engage. Sometimes they would send back a response containing personal info, other times they would politely respond and say they had been contacted in error.
Any Response is Gold
Ideally the scammer wants to get you to share credit card info or bank info, but they don’t need this right away. They are very patient.
Any type of response is huge. That means there is someone on the other end. Bonus points, that someone is willing to have a conversation.
Once they know this, they start digging. My personal email id consists of my first initial, last name and the year I was born. With that info alone, you can do a quick google search and find out my full name, address, phone number, where I worked…One site shows people related to me. And this is what you can do with legitimate public info. Never mind the treasure trove of info available on the dark web.
Be Skeptical
I need to frequently remind my mom and other folks of her era that email addresses, phone numbers and caller id can all be faked quite easily. She’ll fight me and say “no, this is a different person. They have a different email address.” It’s not a different person. This is why it’s called Phishing. Once you nibble on the hook, it is an all out assault to try and reel you in. This will come from many channels and seem like it is coming from different people.
Their Technology is Great
There was a scam here in Massachusetts a year or so ago that got a lot of attention. Scam calls were coming to people’s phones with a caller ID of Mass State Police.
Their investment in technology enables scammers to effectively target us via phone and email and then harvest huge amounts of data about us to fool us and to take our money.
And they can do this at volume. They don’t work on 1 target at a time. They target millions and this process is fully automated.
Let’s Look at an Email Example
When I teach personal finance classes, I put an email up on the screen and ask people to call out things that make them suspicious. Take a look below.
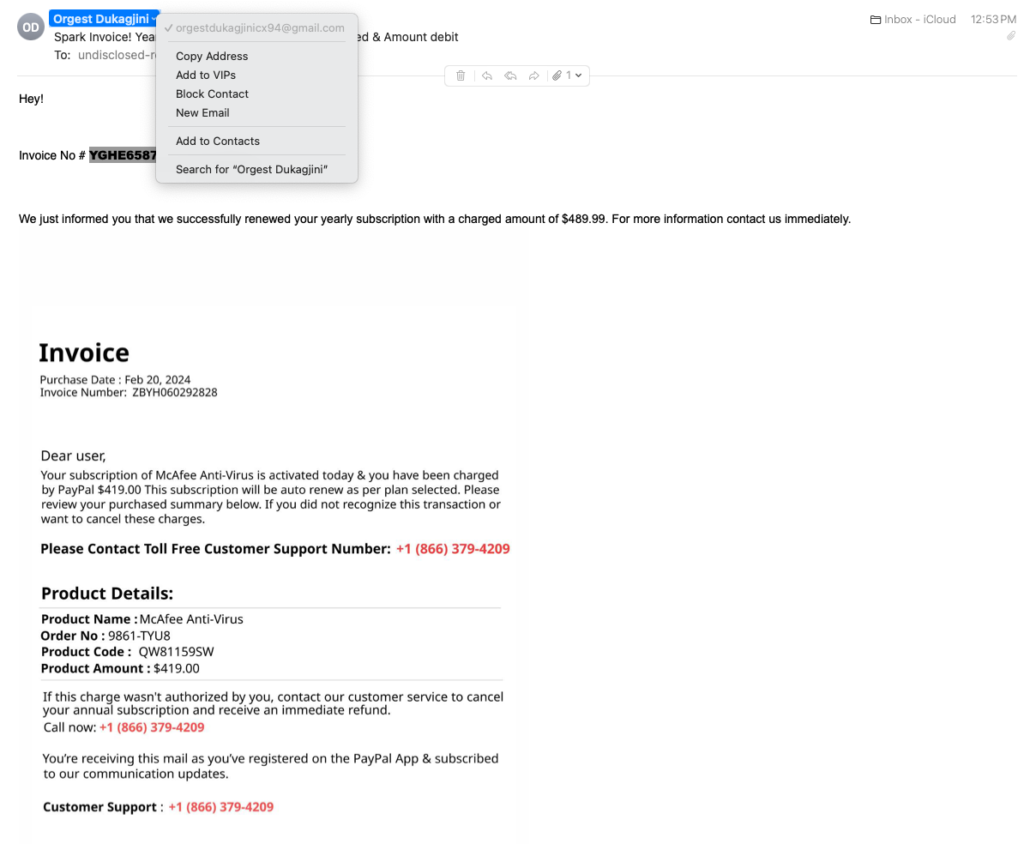
- First thing I like to do is see who is sending this. Most legitimate companies have a strict policy that company communication must come from a company email address so that they can monitor and store customer communication. Orgest – who sent this invoice to me is sending from gmail. That’s suspicious.
- The to: line doesn’t have my email address. it says undisclosed-recipient. That’s suspicious.
- The greeting is strange “Hey” with no name. Legitimate companies don’t use Hey and will generally use your full name.
- You don’t need to be an english major to recognize that the grammar throughout is a little off. Legitimate companies go through great pains to make sure any email from them is clear and professional. They generally catch this stuff.
- Nice that he included an invoice number, but it shows in 2 places and they don’t match.
- The subject says Spark invoice but the body of the email says it is McAfee.
- There is no logo or company name.
What else did you find? Post comments below.
Here’s another one. What’s new in this one that we didn’t see above?

Much better quality. It looks like it could be legit. It has a logo, good use of color and shading. Could be legit???
- It showed in my inbox as coming from Account services, but you can see here it’s a crazy email address.
- Dear…followed by an email address. A company will know your name. Addressing you by an email address is a dead giveaway.
- Grammar and capitalization is kinda funky.
- Why is it sending me to the paypal site to click on help rather than providing a link. This is lazy. A legit company would make it easy.
- Who is the New York State Dfont?
A quick look can identify potential trouble-spots. Be skeptical.
Don’t Click
Aside from looking to engage you in a discussion and get you to turnover personal info, scammers are often looking for ways to install spyware on your computer. Our friends at Apple and Microsoft do a pretty good job securing their operating systems, but the scammers are finding cracks to slip through faster than Apple and Microsoft can plug them. This means each of us needs to be diligent.
Spyware often arrives via an email. The recipient is tricked into clicking a link that may take them nowhere or may go to a dummy web page, but in the background, software is being downloaded and installed. This software may record your keystrokes. This is known as a key-logger. It has access to anything you type (like passwords).
Or the spyware may search through your hard drive for interesting personal or financial information. In either case, it will have the capability to transmit this information back to the scammer. Pretty frightening.
Don’t click is a good rule. Most spyware needs you to take an action for it to install and activate.
If you are unsure, you can always go directly to the website. If you had received the email above regarding your Paypal account and you weren’t sure if it was legit, delete the email, and log into your Paypal account via the app or your web browser and check.
Admin Privileges
Most of the things we do on a computer do not require special privileges. We can open a web browser, navigate to a website, play music, or save a spreadsheet. But when we want to install software, the computer requires us to have administrator privileges. Since we typically have personal computers – meant to be used by a single person or small group like a family, the admin privilege is typically enabled by default. This means when we buy a copy of turbotax, we can install it.
On my computer, I turn this off for my account and I create a new admin account that I use when I install anything. I never log in to the admin account, but when I install a program, a pop up box appears on my screen asking me to log in as an administrator. I enter the admin ID and password and the software installs.
This prevents me from inadvertently installing something. I’m sure there are some clever hackers who’ve found a way around this, but it is a good safety precaution.
Wrap-up
Be careful! Emails that try to trick us are common, but some do a great job posing as legitimate. When we see an email with the amazon logo that says our account has been charged, it is tempting to click. With a little caution, and the tips above, you should be able to spot a fake email.
More to come on other ways scammers target us.
Share your experience or post comments below.
Update 2/29/24: Read here for The Daily Upside‘s article on Biden Wants to Stop Foreign Spies Buying Americans’ Data.
It is important for anyone who uses the internet (that’s you) to understand what a data broker is and what they do. Companies are out there gathering up each of our personal and behavioral (who are we, where do we live, what do we shop for, what do we read…) information and selling it to anyone with a checkbook. Hurray that we are looking to block the selling of our data to foreign spies, but what about the data that is sold locally in the US, what about 3rd party sellers who may find loopholes to sell this data.
We need to be aware that the ability to harvest our data exists. What we do on the internet is not private and can be linked together to get a pretty comprehensive profile about us. Scary. Be safe.